 What is a virus and is it the same as malware?
What is a virus and is it the same as malware?
Malware describes software designed to act maliciously on a computer. The name ‘malware’ is a shorthand for ‘malicious software’ and describes exactly what it is. A computer virus is a single type of malware that can cause harm to your PC, but it is only one of many. Other types of malware are listed below.
Adware
Short for advertising-supported software, adware is a type of malware that delivers adverts to your computer. These advertisements often pop-up and are intrusive, irritating and designed to trick you into clicking something you don’t want. A common example of malware is pop-up ads that appear on many websites and mobile applications.
Adware often comes bundled with “free” versions of software that uses these intrusive advertising to make money. Commonly it is installed without the user’s knowledge and are purposely made to be difficult to remove.
Spyware
Spyware is designed to spy on the user’s activity without their consent or knowledge. Spyware is often installed in the background, collects keyboard input and can harvest data from the computer, monitor web activity and more.
Spyware typically requires installation to the computer. This is commonly done by tricking users into installing the spyware themselves instead of a software application that they thought they were getting. Victims of spyware are often be completely unaware of its presence until the stolen data is used elsewhere (ie in a fraudulent bank transactions or stolen online accounts).
Virus
A computer virus is a form of malware that is installed inadvertently, causing damage to the computer and / or user. A typical virus may install a keylogger to capture passwords, logins and bank information from the keyboard or it might steal or delete data, interrupt programs or cause the computer to crash.
Modern virus programs commonly use your computers processing power and internet bandwidth to perform illegal tasks remotely for hackers. The first sign of this can be when the computer sounds like it is doing a lot of work when no programs are running. A computer virus is often spread through installing unknown software or downloading attachments that contain more than they seem.
Ransomware
Ransomware is a very malicious variety of malware that prevents the user from accessing their own files and data until a ransom is paid. Files within the system are often encrypted with a password that won’t be revealed to the user until they receive money usually in the form of bitcoin.
Instead of accessing the computer as normal, the user is presented with a screen which details the contact and payment information required to access their data again.
Ransomware is typically downloaded through malicious file attachments, email or through a vulnerability in the computer system.
Worm
Another type of malware is the computer worm. Worms spread across computer networks by exploiting vulnerabilities within the operating system. Often these programs harm their host networks by consuming large amounts of network bandwidth, overloading computers and using up all the available resources.
While similar to a virus a worm is able to both copies of itself and spread independently. A virus must rely on human activity to run a program or open a malicious attachment while worms can simply spread over the network without human intervention.
If you would like to make your business secure from malware, give us a call at 08 8326 4364 or via email on su*****@dp*********.au.

 Protecting your business against the latest IT threats should always be a top priority. Updating your antivirus and keeping your operating system and applications up to date is a great way to start. What happens though, when a threat appears at your door before security firms have had a chance to catch it?
Protecting your business against the latest IT threats should always be a top priority. Updating your antivirus and keeping your operating system and applications up to date is a great way to start. What happens though, when a threat appears at your door before security firms have had a chance to catch it? Conventional wisdom says that messy work spaces lead to a disorganised mind. Mess prevents productivity and begins to hamper your professionalism. Shouldn’t that also apply to the computer desktop?
Conventional wisdom says that messy work spaces lead to a disorganised mind. Mess prevents productivity and begins to hamper your professionalism. Shouldn’t that also apply to the computer desktop?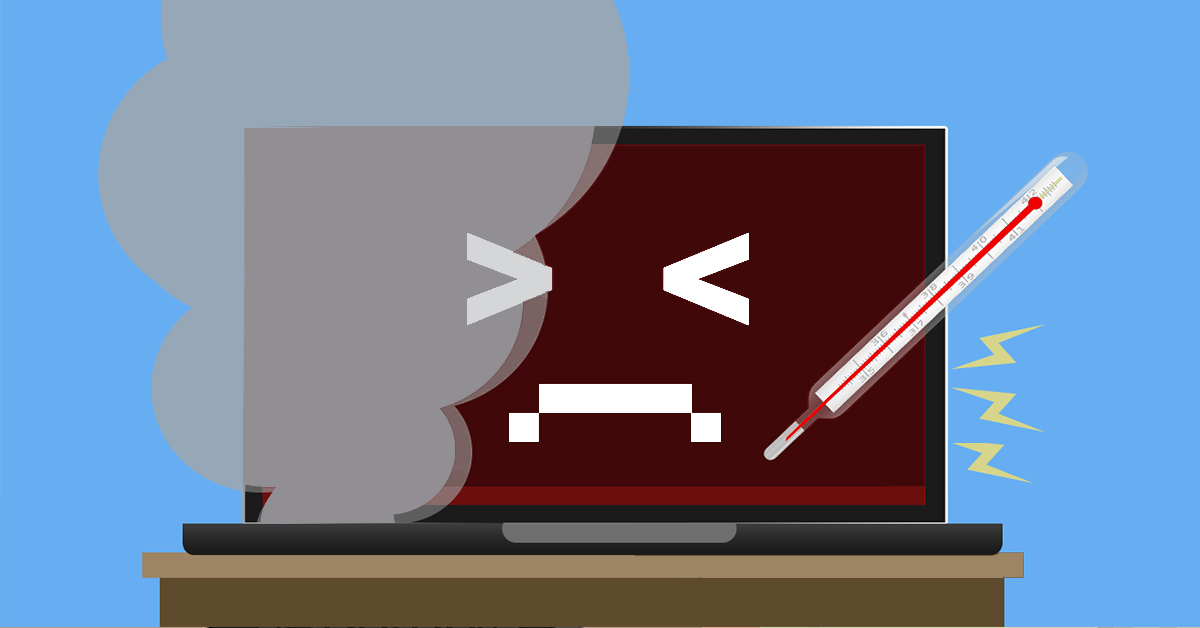 Laptop computers commonly heat up in normal operation. Electronic components, including large capacity batteries, become warm in use but your laptop should never become too hot to handle.
Laptop computers commonly heat up in normal operation. Electronic components, including large capacity batteries, become warm in use but your laptop should never become too hot to handle. When considering IT threats to your business many articles focus on external sources such as hackers. While these dangers are real, in many cases, the largest threat to a firm comes from inside the business itself.
When considering IT threats to your business many articles focus on external sources such as hackers. While these dangers are real, in many cases, the largest threat to a firm comes from inside the business itself. Considering a new technical support service? Find out why you should choose a tech support service that is proactive instead of reactive, what it should look like in the context of your business and how you can make an informed decision.
Considering a new technical support service? Find out why you should choose a tech support service that is proactive instead of reactive, what it should look like in the context of your business and how you can make an informed decision. Being engaged in business used to mean staying wired in at the office eight to twelve hours a day. In today’s world this is completely untrue as often the most efficient workplace is one that is spread far and wide and always on the go.
Being engaged in business used to mean staying wired in at the office eight to twelve hours a day. In today’s world this is completely untrue as often the most efficient workplace is one that is spread far and wide and always on the go.