A common roadblock that many small businesses face is managing their IT needs. If your business relies heavily on the internet, any issues with the network could significantly affect productivity for that day. Another important factor is the sensitive information you have stored on your computer. Any data loss or security breaches could result in lost revenue or damage to the brand. Continue reading
Monthly Archives: November 2019
7 Things You Need to Know About Ransomware!
Ransomware is a when cybercriminals kidnap your data (via encryption) and then demand money so that you can decrypt your own data. It sounds scary and it certainly is! Here are the top seven things you need to know about ransomware. Continue reading
What Can You Do When Your Equipment Fails?

Your business has invested heavily in information technology and you depend on this equipment to support your business. Then the inevitable happens and the equipment fails and you are left scrambling to find a replacement solution. It is a tough place to be in, but it can also provide your business with an opportunity. Continue reading
The Pros and Cons of BCC
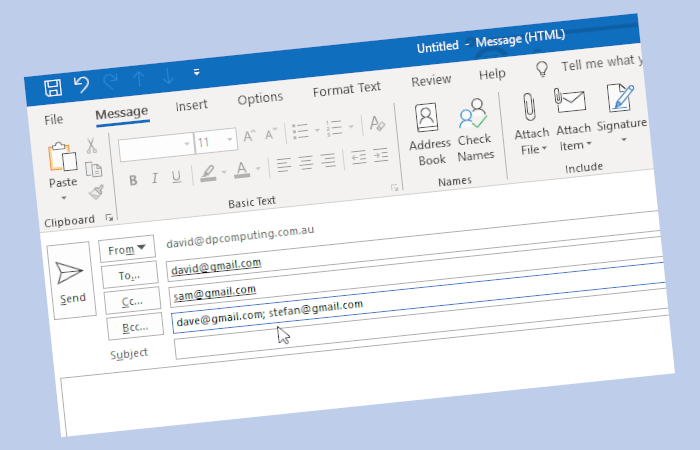 Most people have at some point, “replied all” when meaning to reply to only one person. It is definitely embarrassing, can be a major privacy issue and aggravates those people with emails flooding their box. Another common email gaffe is misusing the CC and BCC fields in outgoing messages – this “little” mistake can prove costly for business. Continue reading
Most people have at some point, “replied all” when meaning to reply to only one person. It is definitely embarrassing, can be a major privacy issue and aggravates those people with emails flooding their box. Another common email gaffe is misusing the CC and BCC fields in outgoing messages – this “little” mistake can prove costly for business. Continue reading
To Upgrade Windows 7 or Not?
Should You Get Rid of Windows 7 and Server 2008?
What If You Don’t Switch?
On January 14, 2020, Microsoft will end its support for Windows 7 and Server 2008. But just because you can continue to use Windows 7 after the end of life date, it doesn’t mean you should. Businesses who rely on technology to keep them running are proactively upgrading their Windows environment to avoid downtime, user issues, loss of functionality with other applications and increased security vulnerabilities. Continue reading



