Efficiency, productivity, and innovation are some of the key differentiators that can propel small businesses forward. Microsoft has expanded the availability of one of its most dynamic tools to SMBs. A tool that can be a real game-changer for growth. Continue reading
Category Archives: News
We Are 30 Years Young!
30 years ago today (16/6/23), DP Computing was born. Continue reading
Windows 11 – Is It Worth The Upgrade?

Microsoft recently introduced Windows 11 as the company’s latest operating system. When compared to Windows 10, this new OS has variety of features that can increase your productivity and provide a better user experience. Continue reading
4 Things Your IT Partner Wishes You Did

Making your IT support team’s life a little bit easier will free up their time, so they can spend more of it proactively protecting your business and its data.
Here are four things that you can start doing to make their life a little bit easier. Continue reading
8 Cyber Security Tips To Help Secure Your Business

Cyber security and Internet attacks has been all over the Australian media recently after the recent press conference from The Prime Minister – Scott Morrison. During the press conference, he mentioned that Australian Businesses, government agencies and other entities are under an active cyber attack campaign by a “state-based actor”. Scott didn’t elaborate too much on who they are but urged businesses to check and if needed increase their cyber security. Continue reading
Is Your Business Ready for the Coronavirus?
The Coronavirus (which is now being called COVID-19) is spreading and we will be feeling the effects for a while. As such, businesses should start to make preparations on how to handle things. Your first priority should be for the health of your employees and customers. Then you need to consider business continuity and prepare for mobile or remote working capabilities for you and your staff. Continue reading
5 Ways the IoT Can Be Used to Streamline a Business
 In just a few years, the Internet of Things (IoT) has gone from being a concept used in science fiction into what can be considered as everyday technology. Continue reading
In just a few years, the Internet of Things (IoT) has gone from being a concept used in science fiction into what can be considered as everyday technology. Continue reading
The nbn™ Effect
For this blog article we are lucky to have Chris Gregory. Chris is the nbn Local Manager for SA/NT and in this article he talks about the NBN effect and how it will benefit your business.

The nbn™ effect
Connectivity is set to spur up to 80,000 new businesses by 2021.
New businesses, jobs and productivity via the nbn™ broadband access network projected to boost Australia’s GDP by up to $10.4 billion.
Australia is in the grip of a nation-wide digital transformation with new research revealing the “nbn™ effect” is projected to contribute to the creation of up to 80,000 new businesses by 2021.
Commissioned by NBN Co and conducted by data analytics and economic firm AlphaBeta, the Connecting Australia report is the nation’s first social and economic study into the impact of the nbn™ broadband access network.
The research shows the growth of new businesses in regions connected to the nbn™ access network accelerated at twice the pace of the national average with up to 5400 additional new businesses created in 2017.
More here.
Providing the right tools for businesses to get the job done
Launch of nbn’s Business Operations Centre, the ‘nerve centre’ of our customer service and support initiatives for business customers. With a dedicated team of more than 100 service experts, this operations centre will be the ‘one-stop shop’ to support the needs of business end customers migrating to and using the nbn™ access network.
More here.
How Australian’s are using the nbn™ access network
With four million end-user premises now activated on the nbn™ broadband access network, now is a great time to take a look at how Australians are using our network.
Download discoveries: median data consumption came in at 108GB while average consumption was 190GB for the month; 14 per cent of end-user premises accounted for 50 per cent of total traffic
Upload findings: median upload total came in at just less than 7GB a month, the average, again, soared (this time to 17.45GB) as one per cent of end-user premises squeezed a lot more (164GB a month) out of their connections
Real-time entertainment usage: Typically the vast majority of traffic demand on NBN Co’s networks comes from live streaming, web browsing and tunneling (usually via virtual private network technology for the purposes of security); end users on HFC / FTTN / FTTP networks all had very similar usage demands, particularly on higher speed plans.
Fixed Line access technology patterns: fixed Line technology choice is not having a great impact on end-user demand today, but that we must continue to ensure flexibility in the capacity management of the network to meet the demands of the future.
More here.
Why an nbn™ powered plan is good for your business
For this blog article we are lucky to have Chris Gregory. Chris is the nbn Local Manager for SA/NT and in this article he talks about the NBN and how it will benefit your business.

Guide to switching your business
Whether you just need basic internet access, or you’re planning a business-wide digital strategy, an nbn™ powered plan is needed for your connectivity.
As you know, the nbn™ broadband access network is being rolled out area by area. As each area becomes ready for service, affected services will have up to an 18-month window – your ‘ready for service’ window – before they are disconnected, so it’s important you switch affected services before your disconnection date, even if you only use a landline phone.
And always remember – the nbn™ access network is a wholesale only network. Your phone and internet providers on-sell nbn™ powered plans to you.
- Contact your Service Provider to discuss your specific business needs to ensure you get the most appropriate and effective solution for your business
- Identify the telecommunications and data services your business requires. These services could include, multiple phone lines, EFTPOS terminals or cloud services
- Establish the business equipment you will want connected to the network – eg security systems, fire alarms, printers or data backup solutions
- Contact the equipment providers to make sure they are compatible with services over nbn™ network
- If you’re a small business or operating out of home, consider the best installation spot and optimal Wi-Fi coverage conditions
More information & support on how to make the switch, visit here
Why an nbn™ powered plan is good for your business
Whether you just need basic internet access, or you’re planning a business-wide digital strategy, an nbn™ powered plan is fundamental.
The role the nbn™ access network plays in your digital future will largely depend on the size of your business.
You’ll also need to consider the degree to which your data speeds and connectivity options affect the experience of your customers—as well as the interactive applications you use, such as video conferencing, 24/7 e-commerce applications and a wide variety of cloud-based services.
Better connectivity opens up new opportunities for your business and can transform the way you interact with customers and suppliers.
 More information & support on nbn™ access network for small and medium business, visit here.
More information & support on nbn™ access network for small and medium business, visit here.
Wholesale broadband traffic classes – why they’re important to your business
For residential users, the switch to the nbn™ access network is relatively straight forward. However, business users will have a range of options to consider—including switching to a solution on the nbn™ access network and/or looking at other connectivity options in the market.
When a phone and internet provider develops business (and residential) plans using the nbn™ access network, those plans are constructed from two basic wholesale ingredients—the first of which is a Traffic Class, the second, a Service Level Agreement (SLA) between nbn and the provider.
nbn offers three Traffic Classes that vary in capability, performance and priority at a wholesale level. For your business, this is all about quality of service options. By combining different wholesale Traffic Classes with optional enhanced SLAs between providers, businesses can choose from a variety of connectivity plans to suit their specific needs.
It all depends on what is available to you, what works for you, and how you decide to integrate the nbn™ access network into your business.
Read more here.
Service level agreements – why they’re important to your business
You’re probably familiar with Service Level Agreements (SLAs), which cover fault rectification, when it’s available and how long it takes to resolve.
For fault trouble tickets raised between 8am and 5pm on business days, the Standard Service Level for all nbn™ services available to phone and internet providers applies (see table below).
If your business has critical data needs, we recommend you speak with your phone and internet provider about having enhanced Service Level Agreements (eSLAs) in place with nbn in relation to your bundle or package. This means nbn will provide a higher level of support to your provider, who in turn should be able to provide a higher level of support to you.
The right questions to ask your phone and internet provider: make sure the plans your phone and internet provider suggest are the right size for your business’ data needs. You may find that for some low-priority business services, a plan based on the residential ‘best effort’ service quality plus an eSLA in place between nbn and your provider meets your needs. While for voice services, you might look at a plan based on a higher quality of service option, which are designed to primarily support voice communication.
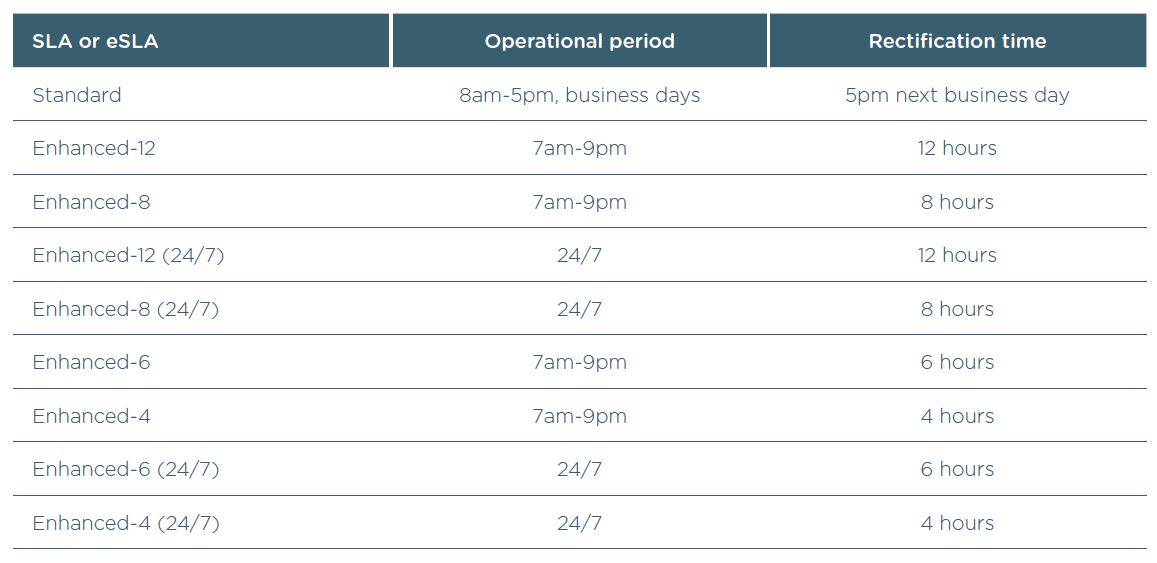
Read more here.
Why Your Business Needs a Firewall With Unified Threat Management
 Unified Threat Management (UTM) is a special kind of firewall solution focused on proactive protection. Consider it like a team of virtual bodyguards that stand at the door between your business and the internet, keeping trouble out while your legitimate traffic can come and go normally.
Unified Threat Management (UTM) is a special kind of firewall solution focused on proactive protection. Consider it like a team of virtual bodyguards that stand at the door between your business and the internet, keeping trouble out while your legitimate traffic can come and go normally.
With the increasing number of connected devices in your business network and the different ways your employees can now connect, it is more important than ever to set up dedicated security systems that give integrated protection. UTM is a series of solutions that work together, simultaneously layering your protection across the board. We’ll cover the four main inclusions here and show exactly what they can do for your business.
Robust Firewall
Put simply, a firewall keeps an eye on all the data coming in and out of your network and looks for anything abnormal. While every home PC comes with a software firewall built in, those ones pale in comparison to what a UTM firewall can do. Remember the team of virtual bodyguards? Imagine the home firewall asking nicely if the data should be doing that, while the UTM slams the data to the ground and demands answers. Its job it to make sure the data entering your network is safe, that it is not part of a cyber-attack, and that in the rare event your network becomes infected, your servers aren’t being used to attack another business.
Anti-virus Where it Matters
With so much new malware being released daily, it’s easy to fall behind in updates and discover you’ve been infected. Your employees are likely doing their best, but manually scanning each file can be exhausting and time-consuming. Your UTM anti-virus is built into the firewall, ensuring known or suspicious malware is stopped at the door removing any risk. Clearly that is the best outcome possible and will allow your employees to work at maximum efficiency, while you can run your business with confidence.
Spam Blocking
Most cyber-attacks come via email these days, with either an attachment or a link. Once clicked, the malware wreaks havoc in your network. Obviously, your employees are smart enough not to open random attachments/links, so hackers use phishing emails. These are emails that look legitimate and may refer to vendors you use, financial services you have accounts with or even seem to be from other employees. Your UTM strips down each email and checks it against high-tech legitimacy markers. If it sees anything suspicious, the email is marked as spam and either held for review or bounced away.
As the phoney emails are blocked, your employees never see the emails so they can’t accidentally open up the network for attack. While the UTM is monitoring for phishing/fake emails, it’s also culling out the general spam that clogs up inboxes. Employees will no longer have to spend precious minutes each day wading through the junk, and the likelihood of missing an important customer email has greatly dropped.
Content Filtering
In a perfect world, your employees would only access work-related sites and do work-related things online. Content filtering can help you limit the risk they’re bringing into your business via their Internet browsing. Your UTM can be set to restrict sites that infect computers, such as adult content, gambling or illegal downloads. It can also be used to restrict access to social media sites like Facebook, Twitter or Pinterest, either during work hours or completely. It’s up to your policies how much you’d like to filter and whether to add any flexibility. Some businesses allow social media during lunch breaks or have special reward hours each week. Simple tweaks like this can increase productivity overnight and give you the security you’re looking for.
You can see how a layered security solution like UTM provides a space for your business to thrive, where systems are secure, employees are able to maintain efficiency, and cyber problems stay outside the doors. The way the layers work together is more effective than a patchwork of separate systems, and a UTM is much easier to configure and maintain.
We can find the right UTM solution for your business. Call us today at 08 8326 4364 or su*****@dp*********.au!



