Cybersecurity is like a jungle: a sprawling, bewildering landscape that businesses find hard to explore. As an IT Provider, we understand the uncertainty that comes with trying to navigate the complex world of cybersecurity. The jungle is vast, with threats hidden in the undergrowth if you set anything up incorrectly and the path to safety (and compliance) is not clear. Continue reading
Tag Archives: cyber security
How To Spot Malicious Website URLs
When browsing the web, using social media or checking your email, it is very important to exercise caution when clicking on links. Cybercriminals actively create deceptive links to infect devices with malware or steal personal information. Continue reading
The Risks of QR Codes
Quick Response (QR) codes have been around for over 20 years, but were not used a lot until recently. During the COVI-19 pandemic, businesses needed a safe, contactless solution and QR codes provided an easy way for customers to access menus, place orders, log into WiFi and more – all without touching shared surfaces. Continue reading
Do You Really Need It All? Understanding the Need for Comprehensive Cybersecurity
As a small business owner, your top priority is keeping costs low while supporting business growth. Your IT provider recommends investing in a robust stack of cybersecurity software and owners wonder whether they really need all those solutions. Continue reading
What Cybersecurity Issues Are Hiding In Your Business?
We are tend to ignore or put off issues that we don’t know about, think are too hard to fix or believe it won’t happen to me. Here are some of the most common cybersecurity issues faced by SMBs that that could leave your business in danger if left unchecked. Continue reading
eBook – Top Tech Scams Exposed
Shield Your Business from Tech Scams
 Discover the essential strategies to protect your business from tech scams with our comprehensive eBook, “Top Tech Scams Exposed”.
Discover the essential strategies to protect your business from tech scams with our comprehensive eBook, “Top Tech Scams Exposed”.
In this free resource, you will gain expert insights into common scams, and practical tips to safeguard your business like:
- Identify common tech scams and stay one step ahead.
- Learn actionable techniques to stop scams in their tracks.
- Gain invaluable knowledge to protect your business from cyber threats.
Do not let scammers put your hard work at risk. Take control of your business’s security today. Click here to instantly download our eBook and fortify your defences against scams.
Anatomy of a Phishing Email
Don’t Get Hooked! Learn How to Spot Phishing Emails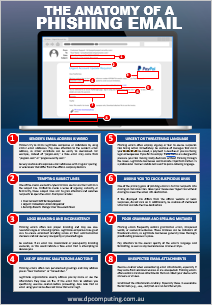
Are you constantly wondering if an email inbox is legitimate or a cunning phishing attempt? Continue reading
Combatting Security Fatigue
I know I keep on going on about security and you keep getting prompted for another password change or to install another security update. These are frustrating and can lead to cybersecurity fatigue. You can’t stop securing your tech and doing updates, but what can you do to combat both your own and your employees annoyance with the process. Continue reading
Protecting Yourself From Identity Theft
Many everyday objects can lead to identity theft and they can often get overlooked because your focus is on your computers and cloud accounts. Yes, it is important to have strong passphrases and use antivirus on your PC, but you also need to be wary of other ways that hackers and thieves can get access to your personal data. Here are six common things that criminals can use to steal your information. Continue reading
Are Your Cloud Accounts Configured Correctly?
Misconfiguration of cloud solutions is often overlooked when companies plan cybersecurity strategies. Cloud apps are typically quick and easy to sign up for and the users assume that they do not need to worry about security because it is handled by the provider. This is an incorrect assumption because cloud security is a shared model. The provider of the solution handles securing their backend infrastructure and the user is responsible for configuring security settings in their actual account. The problem with misconfiguration is huge and is the number one cause of cloud data breaches. Continue reading








