You can find QR codes are everywhere these days, on restaurant menus, in shops, flyers and posters. QR codes are convenient and easy to use and you can easily scan them with your smartphone camera to go to a website, a coupon, a video or some other online content. Continue reading
Tag Archives: Phishing
The Risks of QR Codes
Quick Response (QR) codes have been around for over 20 years, but were not used a lot until recently. During the COVI-19 pandemic, businesses needed a safe, contactless solution and QR codes provided an easy way for customers to access menus, place orders, log into WiFi and more – all without touching shared surfaces. Continue reading
Anatomy of a Phishing Email
Don’t Get Hooked! Learn How to Spot Phishing Emails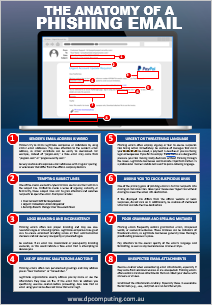
Are you constantly wondering if an email inbox is legitimate or a cunning phishing attempt? Continue reading
7 Tips To Prevent Mobile Malware
Cybersecurity researchers uncovered that mobile malware attacks surged by 500% a the start of 2022. This is alarming both in scale and the fact that many people are not yet protecting their smartphones. Year after year, mobile phones have become more powerful and today can do many of the same functions as a computer – just with a much smaller screen. But people tend to secure their computers much better than they do with their smartphones and this needs to change as over 60% of digital fraud now occurs through mobile devices! This makes all mobile devices a high risk if proper safeguards are not followed. Continue reading
Cybersecurity Attack Trends To Look Out For In 2023
2023 is just about here, and you should start to plan for the new year. Sixty-eight percent of surveyed business leaders feel that cybersecurity risks are getting worse and this is the area you should start to take seriously (if you haven’t already) and look at the attack trends. Continue reading
Small Businesses Are Attacked 3x More Than Larger Ones
As a small business owner do you feel more secure from cyberattacks because of your size?
Maybe you think that you could not possibly have anything that a hacker would be interested in?
Did not think that the bad guy even knew about your small business? Continue reading
6 Ways to Stop Social Phishing Attacks
Phishing is the number one method of attack for everything from ransomware to credential theft. Email phishing is the main method for delivery but other delivery means are on the rise. Continue reading
Phishing Attack Trends to Be Aware of in 2022

Phishing remains one of the biggest dangers to every business’s security as it is the main delivery method for all types of cyberattacks. Cisco’s 2021 Cybersecurity threat trends report shows that at least one person clicked a phishing link in around 86% of organizations and suggests that phishing accounts for around 90% of data breaches. Continue reading







